Private by Design
Enterprise-grade security and compliance built into every layer. Your data stays protected, your team stays productive.
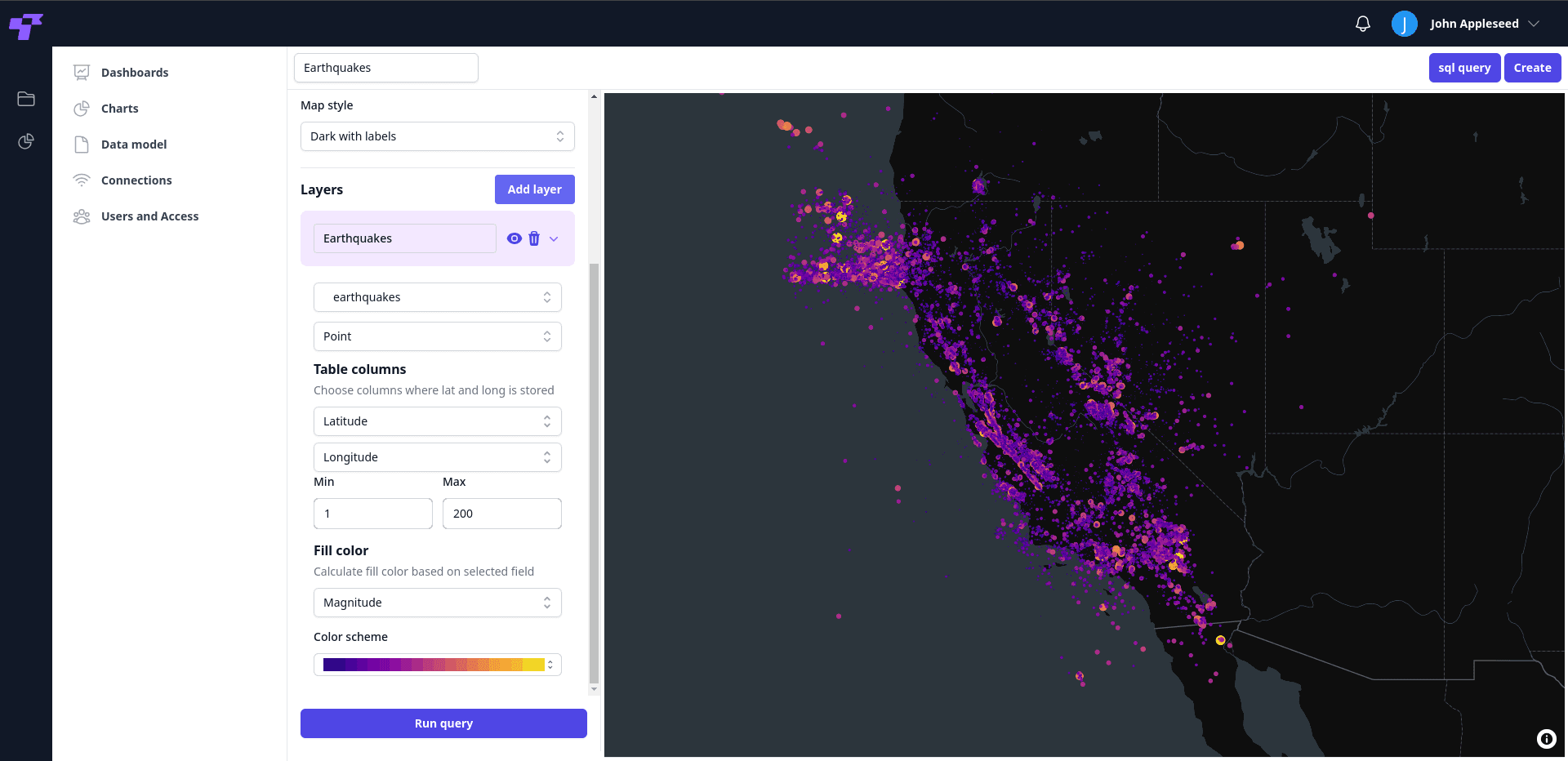
Encryption & Data Protection
AES-256 encryption at rest — Your files, messages, and data are encrypted using military-grade standards.
TLS 1.2+ encryption in transit — All communications are secured end-to-end.
Bring-Your-Own-Key (BYOK) — Business+ plans support customer-managed encryption keys for ultimate control.
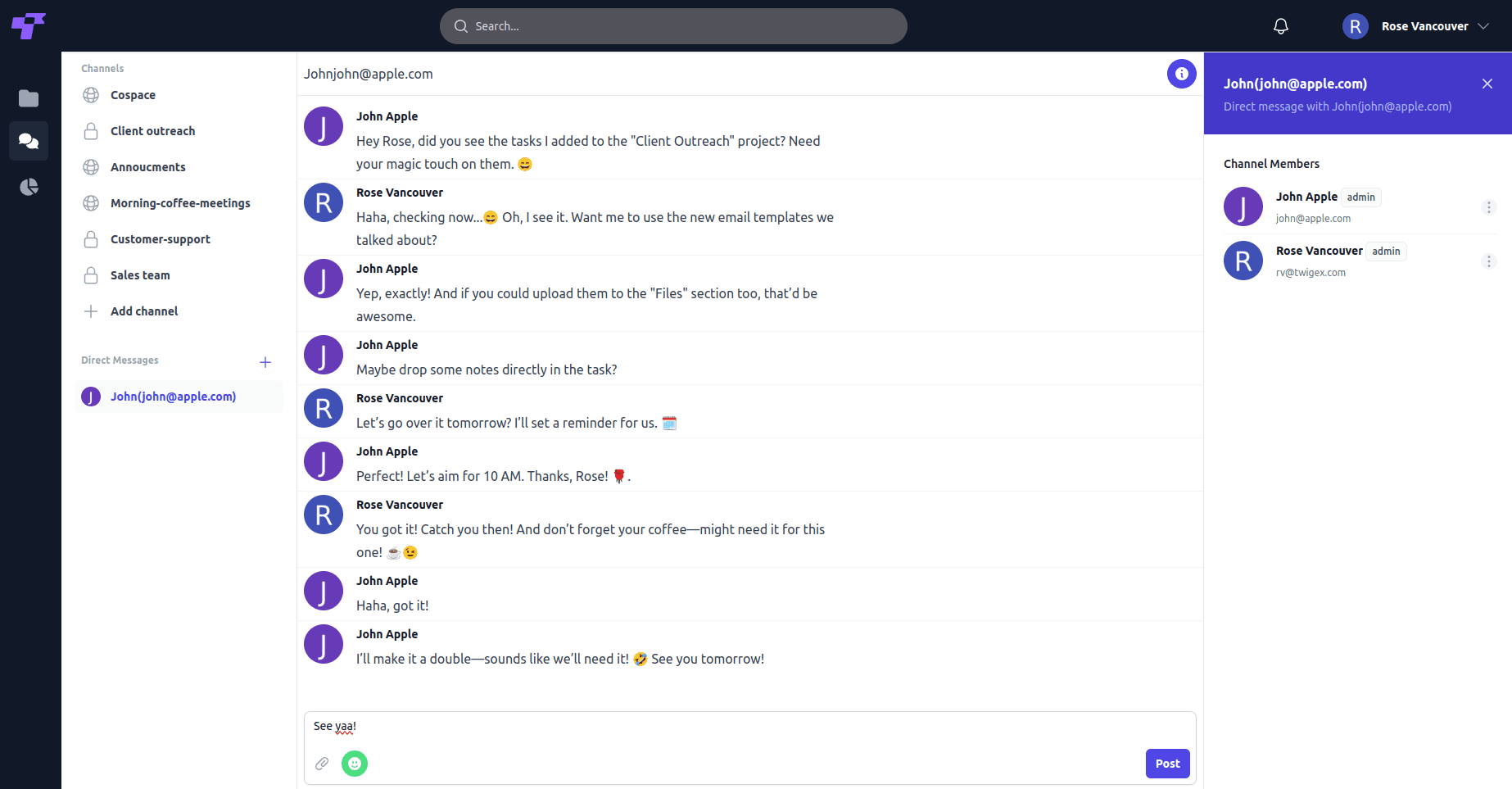
Access Control & Authentication
SSO/SAML integration — Connect with your existing identity provider.
SCIM provisioning — Automated user and group management.
Multi-Factor Authentication (MFA) — Add an extra layer of security with TOTP, SMS, or hardware keys.
Granular role-based permissions — Control access down to individual files and conversations.
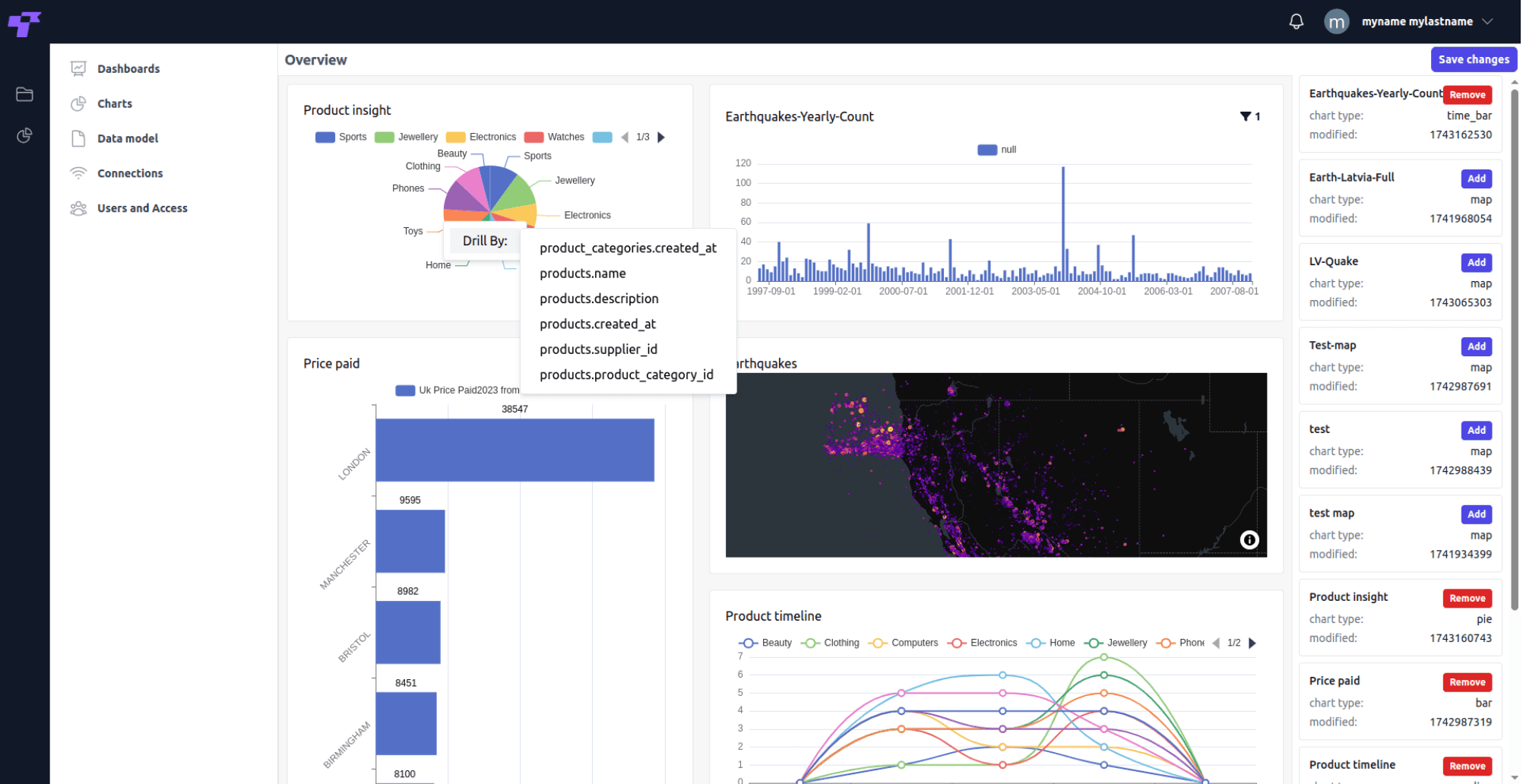
Audit Logs & Compliance
Comprehensive audit trails — Track all user actions, file access, and system changes.
Configurable retention policies — Meet your organization's data retention requirements.
Legal hold capabilities — Preserve data for litigation and regulatory purposes.
GDPR & CCPA aligned — Built-in compliance with global privacy regulations.
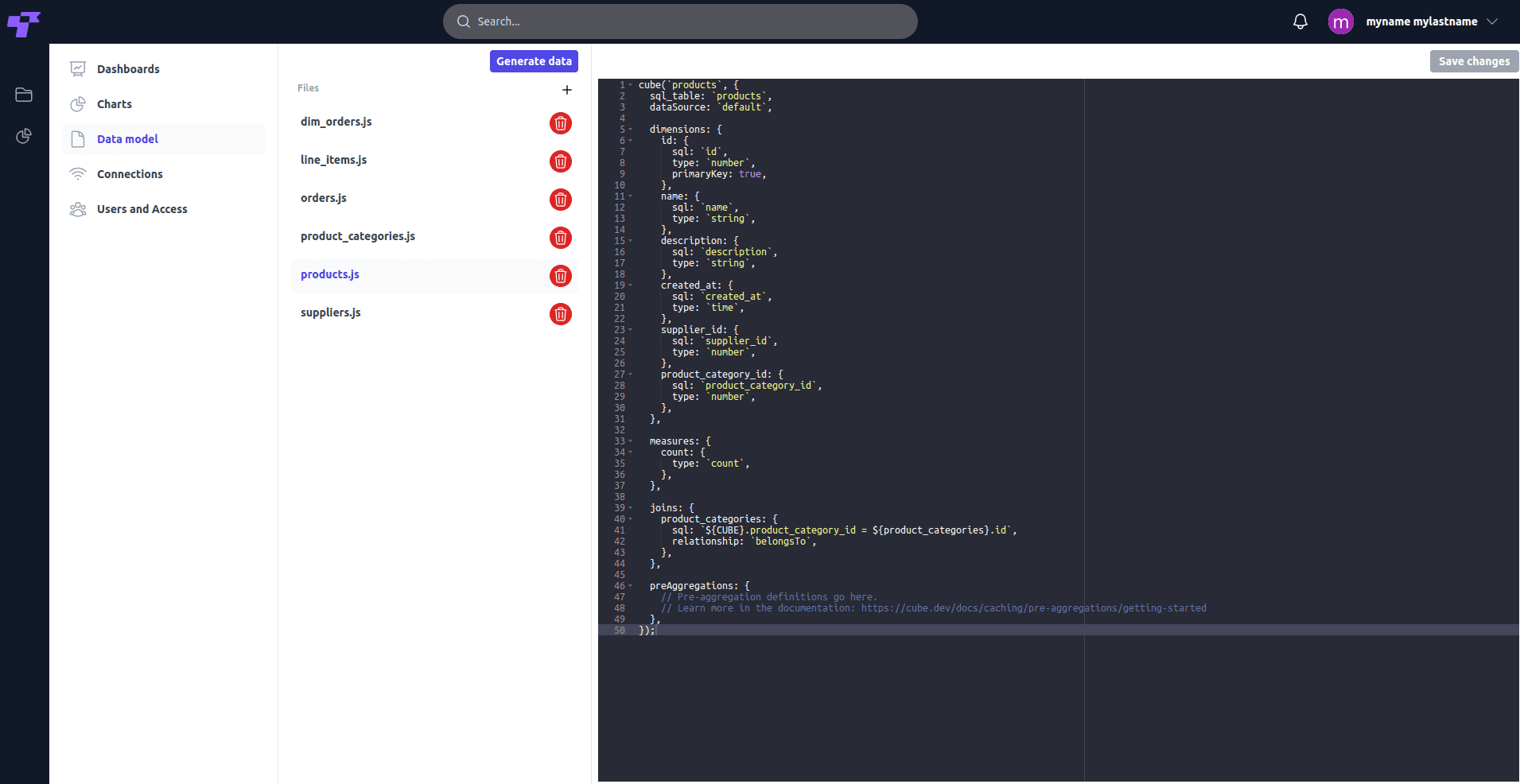
Data Residency & Infrastructure
Choose your data location — Host your data in EU or US regions to meet regulatory requirements.
Standard Contractual Clauses (SCCs) — Compliant cross-border data transfers.
99.95% uptime SLA — Redundant infrastructure across multiple availability zones.
Business+ exclusive features — BYOK encryption and enhanced data sovereignty controls.
Security Testing & Monitoring
Regular penetration testing — Third-party security assessments conducted quarterly.
Continuous security monitoring — 24/7 threat detection and incident response.
Vulnerability management — Proactive identification and remediation of security issues.
Bug bounty program — Responsible disclosure and rewards for security researchers.
Security Resources
Access comprehensive documentation, reports, and tools to evaluate and implement our security measures.
Security Documentation
Detailed technical specifications, architecture diagrams, and implementation guides.
Legal & Compliance
Data processing agreements, privacy policies, and compliance certifications.
Security Testing
Third-party penetration test results, vulnerability assessments, and security audits.
Questions about security?
Our security team is here to help. Schedule a dedicated security review or get answers to your compliance questions.